Step 1 – Create Account
First of all, create a user account for the sftp access. For this tutorial, we are creating a user named sftpuser with no shell access. Also, set a strong password for the user.
Step 2 – Create Directory
Now, create the directory structure to be accessible by sftp user. we will restrict the new user to this directory only. So the user can’t access files to other directories. Change the ownership of the directory to newly created sftp users. So that sftpuser can read and write on this directory. You must set the owner and group owner of the /var/sftp to root. The root user has read/write access on this access. Group members and other accounts have only read and execute permissions.
Step 3 – Configure SSH for SFTP
As we know the SFTP runs over the SSH protocol, So we need to configure this in the configuration file. Edit the SSH configuration file in a text editor. And add the following settings at end of the file. Save the configuration and restart SSH service to apply changes. All done, Your system is ready to accept sftp only connection for the created account. Let’s test the sftp connection and also make sure that the user is not authorized to SSH.
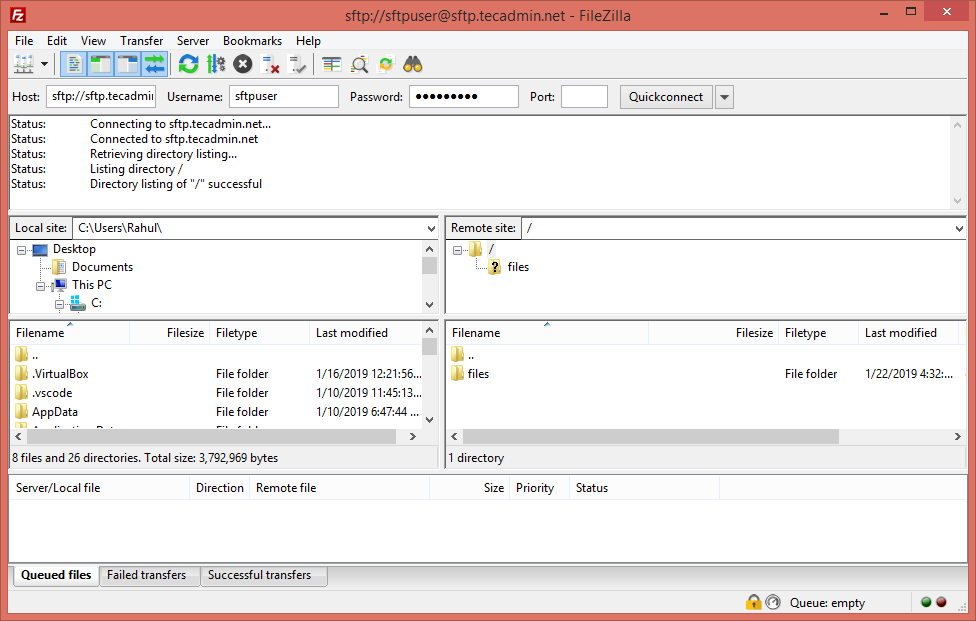
Step 4 – Test SFTP Connection
I am using FileZilla for the connection to the SFTP instance from my Windows systems. Linux desktop users can also use Filezilla for connection. For the Linux server, users can use sftp command-line utility to connect to remote sftp instance. Connect with FileZilla:
This account is configured for SFTP only connection. So if any user tried to connect via SSH will be disconnected immediately after successful authentication. User will get below message: The above message (This service allows sftp connections only.) shows that the user has sftp access only. Users can’t connect server over SSH.